The Essence of Layered Security
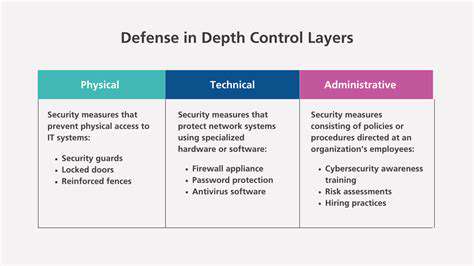
Modern organizations require comprehensive security strategies to safeguard critical assets and operations. Rather than relying on a single protective measure, this methodology employs overlapping security controls that collectively create a formidable barrier against threats. The beauty of this approach lies in its redundancy - if one layer fails, others remain to thwart potential breaches.
Securing the Digital Perimeter
Network security serves as the first line of defense in any comprehensive protection scheme. Modern implementations combine traditional firewalls with advanced detection systems that analyze traffic patterns in real-time. Strategic network segmentation proves particularly valuable, creating digital compartments that contain potential intrusions. This architectural decision significantly reduces the blast radius of any successful attack, protecting mission-critical systems from collateral damage.
Device-Level Protection Measures
Individual endpoints represent vulnerable access points that require specialized protection. Contemporary solutions extend beyond basic antivirus software to include behavioral analysis tools that detect anomalous activities. The combination of complex credential requirements and secondary verification methods creates substantial barriers against unauthorized access. Regular patching of operating systems and applications further reduces potential attack vectors.
Information Safeguarding Techniques
Protecting sensitive data requires both technical solutions and organizational policies. Encryption transforms readable information into secure formats during storage and transmission. Implementing comprehensive data governance policies ensures consistent protection throughout information's entire existence, from initial creation to final disposition. These policies should clearly delineate access privileges based on organizational roles and responsibilities.
Human Factor Considerations
Employee education programs transform staff members from potential vulnerabilities into security assets. Effective training goes beyond basic awareness to develop practical skills in threat recognition and response. Since social engineering attacks frequently target human psychology rather than technical systems, an educated workforce provides a crucial defensive layer.
Emergency Response Preparation
Well-structured incident response protocols enable organizations to react swiftly and effectively to security events. These plans detail specific actions for containment, eradication, and recovery phases. Regular simulation exercises ensure that response teams maintain readiness and can execute procedures under pressure. Documenting lessons learned from these exercises continuously improves the organization's defensive capabilities.
Proactive Risk Reduction
Systematic vulnerability management involves continuous identification and remediation of potential weaknesses. Regular scanning combined with prioritized patching creates a dynamic defense system that evolves with the threat landscape. Establishing routine assessment processes helps organizations stay ahead of emerging threats rather than reacting to breaches after they occur.
Secure Software Development Lifecycle (SDLC) Integration

Fundamentals of Secure Development
The integration of security principles throughout the software creation process represents a paradigm shift in development philosophy. This approach recognizes that security cannot be effectively bolted on after completion but must be woven into the project's fabric from conception. Such integration reduces remediation costs and prevents the accumulation of technical security debt that could compromise future operations.
Coding with Security in Mind
Secure coding practices require developers to think like both creators and protectors. Training programs should emphasize common vulnerability patterns and their prevention techniques. Input validation deserves particular attention, as improper handling of user-provided data represents a frequent attack vector. The use of established secure coding frameworks and libraries can prevent reinvention of security solutions while leveraging community-vetted implementations.
Continuous Security Validation
Integrating security testing throughout development phases creates multiple opportunities to identify and address vulnerabilities. Automated testing tools can be incorporated into continuous integration pipelines, providing immediate feedback to developers. Combining automated scans with manual expert review creates a balanced approach that catches both obvious and subtle security issues. This hybrid methodology ensures thorough coverage without sacrificing development velocity.
Post-Deployment Security Management
Application security requires ongoing attention after release to production environments. Continuous monitoring detects potential breaches or vulnerabilities that emerge during operation. Establishing clear procedures for incident response ensures rapid reaction when security events occur, minimizing potential damage. Regular updates and patches address newly discovered vulnerabilities, maintaining the application's security posture over time.

Continuous Monitoring and Incident Response Plans
Comprehensive Surveillance Systems
Modern monitoring solutions employ sophisticated analytics to detect potential security incidents across complex environments. These systems combine rule-based detection with machine learning algorithms that identify anomalous patterns indicative of malicious activity. Proper configuration ensures these tools provide actionable intelligence rather than overwhelming operators with false positives. Integration with existing security infrastructure creates a unified view of organizational risk.
Structured Incident Handling
Detailed response plans provide clear guidance during security events when time is critical. These documents should outline specific roles, responsibilities, and escalation paths. Regular tabletop exercises maintain team readiness and identify potential gaps in response capabilities. Documenting incident response activities creates institutional knowledge that improves future responses and supports continuous improvement.
Centralized Security Management
SIEM solutions aggregate security data from multiple sources, providing correlation and analysis capabilities that individual tools cannot achieve. Properly configured, these systems reduce mean time to detection and response by highlighting the most critical alerts. Regular tuning ensures the system remains effective as the threat landscape evolves.
Workforce Security Education
Ongoing security awareness programs help employees recognize and resist social engineering attempts. Training should be engaging and relevant, using real-world examples that resonate with participants. Simulated phishing campaigns and other practical exercises reinforce theoretical knowledge with hands-on experience. An educated workforce serves as an organization's human sensor network, detecting threats that technical controls might miss.
Secure Information Exchange
Protecting communications requires both technical controls and policy enforcement. Encryption should be applied to all sensitive transmissions, with key management processes that balance security and accessibility. Regular audits verify that security controls function as intended and identify areas for improvement. Access controls should follow the principle of least privilege, ensuring individuals can only access information necessary for their roles.